**Introduction to Computer Networking - Exam
THE UNIVERSITY OF DODOMA
COLLEGE OF INFORMATICS AND VIRTUAL EDUCATION
Department of Computer Science and Engineering
End of Semester Two University Examination for the 2023/2024 Academic Year
- Course Name: Introduction to Computer Networking
- Paper Code Number: CN 121/CN 120
- Date of Examination: 2nd July 2024
- Time: 11:45 – 14:45
- Duration: 3 Hours
- Venue(s): AUDITORIUM, ELL, LRB 105, LRB 004D, LDR005B, CBSL_AB2_LR01, CBSL_AB1_LR01, CBSL_AB1_LR02, EDU THEATRE 4
- Sitting Programme(s): BSc. TE1, CE1, BIS1, IDIT1, IS1, CNISE1, CSDFE1, MTA1, SE1, CS1, DCBE1, BCOMM1, BAKSET1, BAEEP1, and RED SCIENCE_ICT3
SECTION A: (40 MARKS)
Answer ALL questions in this section.
Question One
Choose the most correct answer.
i. Which one of the following is a true statement about ARP poisoning or MAC spoofing?
- A. MAC spoofing is used to overload the memory of a switch
- B. ARP poisoning is used to falsify the physical address for a system to impersonate that of another authorized device.
- C. MAC spoofing relies on ICMP communication to traverse routers.
- D. ARP poisoning can use unsolicited or gratuitous replies.
Answer (Click to show)
D. ARP poisoning can use unsolicited or gratuitous replies.
ii. Jim was tricked into clicking on a malicious link contained in a spam email message. This caused malware to be installed on his system. The malware initiated a MAC flooding attack. Soon, Jim’s system and everyone else’s in the same local network began to receive all transmissions from all other members of the network as well as communications from other parts of the next-to-local members. The malware took advantage of what conditions in the network?
- A. Social engineering
- B. Network segmentation
- C. ARP queries
- D. Weak switch configuration
Answer (Click to show)
D. Weak switch configuration
iii. Ethernet frame consists of ______
- A. MAC address
- B. IP address
- C. Default mask
- D. Network address
Answer (Click to show)
A. MAC address
iv. A ______ firewall is able to make access control decisions based on the content of communications as well as the parameters of the associated protocol and software.
- A. Application-level
- B. Stateful inspection
- C. Circuit-level
- D. Static packet filtering
Answer (Click to show)
A. Application-level
v. In the OSI model, when data is sent from device A to device B, the 5th layer to receive data at B is
- A. Application layer
- B. Transport layer
- C. Link layer
- D. Session layer
Answer (Click to show)
D. Session layer
vi. How many hosts on a half-duplex segment can talk at one time?
- A. Zero
- B. One
- C. Two
- D. Unlimited
Answer (Click to show)
B. One
vii. You need a network that provides centralized authentication for your users. Which of the following logical topologies should you use?
- A. VLANs
- B. Peer-to-peer
- C. Client-server
- D. Mesh
Answer (Click to show)
C. Client-server
viii. What type of network must a home user access in order to do online shopping?
- A. An intranet
- B. The internet
- C. An extranet
- D. A local area network
Answer (Click to show)
B. The internet
ix. In the layer hierarchy as the data packet moves from the upper to the lower layers, headers are
- A. Added
- B. Removed
- C. Rearranged
- D. Modified
Answer (Click to show)
A. Added
x. Which of the following is an example of a PC LAN access protocol?
- A. TCP/IP
- B. NetBEUI
- C. Ethernet
- D. Token Bus
Answer (Click to show)
C. Ethernet
Question Two
Match the item in Column A with its corresponding item in Column B.
(1 Mark Each)
Column A i. The distortion of a transmitted message due to signals carried in adjacent wires ii. The measure of the usable data transferred across media over a given period of time iii. Converts text-based addresses to and from IP iv. Standard protocol for the Internet v. Broken-down parts of a message sent over the Internet vi. An attempt to make a computer resource unavailable to its intended users vii. Port address viii. Wireless connection that uses light waves over short distances ix. It identifies the device physically in the network. x. Cable that transmits data as pulses of light
Column B
- A. DNS
- B. MAC address
- C. Packets
- D. Fiber cable
- E. Internet Protocol
- F. Throughput
- G. Fiber optic
- H. TCP/IP
- I. Attenuation
- J. IP address
- K. Wi-Fi
- L. Latency
- M. Infrared
- N. Ethernet
- O. Denial of service
- P. TCP/UDP
- Q. Interference
Answer (Click to show)
i. Q. Interference
ii. F. Throughput
iii. A. DNS
iv. H. TCP/IP
v. C. Packets
vi. O. Denial of service
vii. P. TCP/UDP
viii. M. Infrared
ix. B. MAC address
x. G. Fiber optic
Question Three
Write TRUE for correct statement and FALSE for incorrect statement.
(1 Mark Each)
i. An extranet is a network that uses Internet technologies to allow access to invited users from outside the organization.
Answer (Click to show)
TRUE
ii. Infrared rays penetrate through walls.
Answer (Click to show)
FALSE
iii. The data link layer is responsible for end-to-end frame delivery.
Answer (Click to show)
FALSE (It’s responsible for node-to-node delivery)
iv. Optic fibers is one example of copper cabling used in LANs.
Answer (Click to show)
FALSE
v. Delimiting and synchronization of data exchange is provided by session layer.
Answer (Click to show)
TRUE
vi. Microwave transmissions are a line-of-sight medium.
Answer (Click to show)
TRUE
vii. Session layer defines the format in which the data is to be exchanged between the two communicating entities.
Answer (Click to show)
FALSE (This is the presentation layer’s function)
viii. A network architecture provides the blueprint for designing and implementing a network.
Answer (Click to show)
TRUE
ix. The transport layer routes messages through the network selecting the best path from the source to the destination station.
Answer (Click to show)
FALSE (This is the network layer’s function)
x. In star topology every node has a direct connection to every other node in the network.
Answer (Click to show)
FALSE (This describes mesh topology)
Question Four
a. For each of the following, identify the network devices (hub, switch, repeater, router, bridge, NIC) that most closely match the specified characteristics.
(1 Mark Each)
i. This device sends and receives information about the Network layer.
Answer (Click to show)
Router
ii. This device uses hardware addresses to filter a network.
Answer (Click to show)
Switch or Bridge
iii. This device creates one big collision domain.
Answer (Click to show)
Hub
iv. A network device that is used to connect multiple devices together without segmenting a network.
Answer (Click to show)
Hub
v. A network device that provides the physical, electrical, and electronic connections to the network media.
Answer (Click to show)
NIC (Network Interface Card)
b. For each of the following function, identify the OSI layer responsible for each function.
(1 Mark Each)
i. Bit-by-bit delivery in the network.
Answer (Click to show)
Physical Layer
ii. Establishing, maintaining and synchronizing the interaction between communicating devices.
Answer (Click to show)
Session Layer
iii. Physical addressing in the network.
Answer (Click to show)
Data Link Layer
iv. Translation, decryption and compression of information.
Answer (Click to show)
Presentation Layer
v. Provides the network services to the end-users.
Answer (Click to show)
Application Layer
SECTION B: (60 MARKS)
Attempt any THREE (3) out of FOUR (4) questions provided.
Question Five
(20 Marks)
a. Name two types of connectors that are used for each of the following cables:
(2 Marks Each)
i. UTP
Answer (Click to show)
RJ-45, RJ-11
ii. Fibre cable
Answer (Click to show)
SC, LC, ST, FC
b. A small office has twelve (12) workstations that need to be connected. The office also has three (3) printers that need to be accessible to all workstations.
i. Determine the network topology and the number of links required if:
(3 Marks Each)
a. All workstations and printers are connected in a fully meshed topology.
Answer (Click to show)
Topology: Mesh, Links: n(n-1)/2 = 15(14)/2 = 105 links
b. A central switch is used to connect all workstations and printers.
Answer (Click to show)
Topology: Star, Links: 15 links
ii. The workstations are equally distributed into 3 groups, with each group connected to one of the 3 printers using a star topology forming a network segment. Suppose that the network segments are fully interconnected with the others.
a. Sketch the network topology.
(3 Marks)
Answer (Click to show)
Three star networks interconnected in a mesh
b. Determine the number of links in it (a).
(3 Marks)
Answer (Click to show)
Each star: 4+1=5 links × 3 = 15, plus 3 inter-switch links = 18 total links
c. What name best suit the topology in it (a)?
(3 Marks)
Answer (Click to show)
Hybrid Topology (Star-Mesh)
d. How many collision domains are in the network?
(3 Marks)
Answer (Click to show)
15 collision domains (each device port on a switch is a separate collision domain)
Question Six
(20 Marks)
a. What is the subnet address if the destination address is 100.45.34.0 and the subnet mask is 255.255.240.0?
(2 Marks)
Answer (Click to show)
100.45.32.0
b. Your router has the following IP address on Ethernet: 172.16.2.1/23. Determine two valid addresses that can be valid host IDs on the LAN interface attached to the router.
(2 Marks)
Answer (Click to show)
172.16.2.2, 172.16.2.3
c. What is the maximum number of IP addresses that can be assigned to hosts on a local subnet that uses the 255.255.255.224 subnet mask?
(3 Marks)
Answer (Click to show)
30 hosts
d. You need to subnet a network that has 5 subnets, each with at least 16 hosts. Which subnet mask would you use?
(3 Marks)
Answer (Click to show)
255.255.255.224
e. A company is granted the site address 181.56.0.0. The company needs 1000 subnets. Design the subnets.
(6 Marks)
Answer (Click to show)
Subnet mask: 255.255.255.128, 10 bits borrowed (2¹⁰=1024 subnets)
f. A network administrator is connecting hosts A and B directly through their Ethernet interfaces, as shown in figure 1. Ping attempts between the hosts are unsuccessful. What can be done to provide connectivity between the hosts?
(4 Marks)
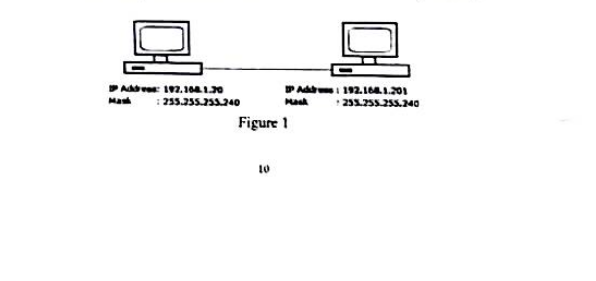
Answer (Click to show)
Solution:
To provide connectivity between Host A and Host B: i. Use a crossover cable (or ensure NICs support Auto-MDIX) for direct connection.
ii. Confirm both IPs (192.168.1.200and192.168.1.201) are in the same subnet (255.255.255.240). iii. Ensure correct configuration (no duplicate IPs).
iv. Disable/allow ICMP through the firewall if enabled.
Question Seven
(20 Marks)
a. Define Network security.
(1 Mark)
Answer (Click to show)
Network security involves policies, practices, and tools designed to protect network infrastructure and data from unauthorized access, misuse, modification, or denial of service.
b. CIAAN provides the core security properties that are used to ensure the security and reliability of information systems including network infrastructure. Describe each concept showing its relevance in securing the network infrastructure.
(5 Marks)
Answer (Click to show)
Confidentiality: Prevents unauthorized disclosure
Integrity: Ensures data accuracy and trustworthiness
Availability: Ensures authorized access when needed
Authentication: Verifies user/system identity
Non-repudiation: Prevents denial of actions
c. Informatics Insurance Company is a firm with its main offices at Dodoma, supporting 300 staff at the headquarters, and 400 staff at the different branches across the country. The company board has decided to revamp the current network at its HQ, and install a new network infrastructure, offering resilient and secure services. You have been hired as a network security consultant to identify threats and propose necessary mitigation mechanisms. Use the TCP/IP model as a guide to accomplish your assignment.
(14 Marks)
Answer (Click to show)
Using the TCP/IP model, threats and mitigations for Informatics Insurance Company are:
Application Layer : Threats include malware, phishing, SQL injection, and weak authentication. Mitigation: deploy firewalls/IDS-IPS, use MFA and strong passwords, patch applications, and train staff in cybersecurity.
Transport Layer : Threats include TCP SYN flooding, session hijacking, and port scanning. Mitigation: configure firewalls to restrict ports, use TLS/SSL encryption, and implement DoS/DDoS protection with rate limiting.
Internet Layer : Threats include IP spoofing, routing attacks, and man-in-the-middle. Mitigation: use IPSec and VPNs, secure routing protocols, and apply router ACLs.
Network Access Layer : Threats include MAC spoofing, ARP poisoning, and unauthorized physical access. Mitigation: enforce port security, VLAN segmentation, 802.1X authentication, WPA3 Wi-Fi, and restrict access to networking devices.
General/Administrative : Enforce security policies, perform regular backups, continuous monitoring, auditing, and establish an incident response team.
Summary of the answers Application Layer: Web filtering, antivirus, secure protocols
Transport Layer: Firewalls, TLS/SSL encryption
Internet Layer: IPSec, VPNs, router ACLs
Network Access Layer: MAC filtering, port security, physical security
Question Eight
(20 Marks)
a. What is the name of a Windows command line utility that can be used to display TCP/IP configuration settings?
Answer (Click to show)
ipconfig
b. Which two commands in MS Windows are used for resetting the IPv4 DHCP configuration settings for all adapters?
Answer (Click to show)
ipconfig /release and ipconfig /renew
c. A command line utility in MS Windows used for displaying protocol statistics and current TCP/IP network connections is called?
Answer (Click to show)
netstat
d. Which command in MS Windows is used to display the contents of a routing table?
Answer (Click to show)
route print
e. Which option allows for execution of a command if the requested operation in the command line interface in MS Windows requires elevation?
Answer (Click to show)
Run as Administrator
f. What is the name of a command line utility used for checking the reachability of a remote host?
Answer (Click to show)
ping
g. Which command in MS Windows is used to display help information related to a specific network command line utility?
Answer (Click to show)
command /? or help command
h. A network command line utility in MS Windows that tracks and displays the route taken by IPv4 packets on their way to another host is called?
Answer (Click to show)
tracert
i. Which command in MS Windows displays a table consisting of IP addresses and their resolved Ethernet physical addresses?
Answer (Click to show)
arp -a
j. Which command allows for obtaining a domain name to IP address mapping in MS Windows?
Answer (Click to show)
nslookup
END OF EXAMINATION PAPER